Our Service Offerings
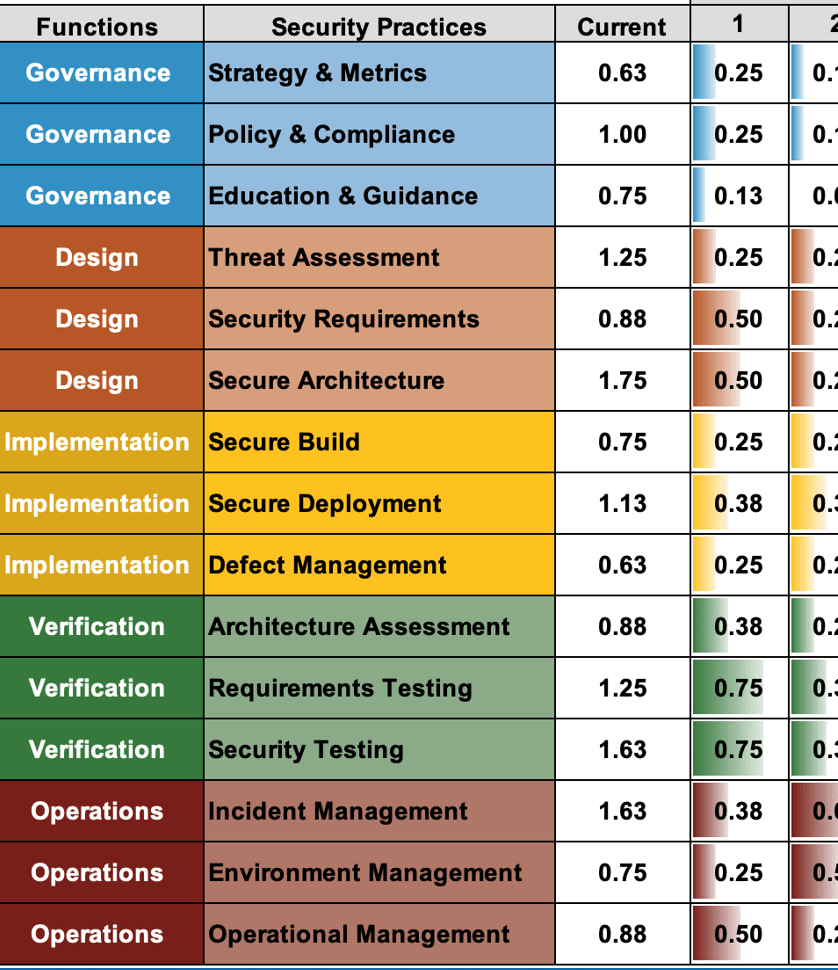
Software Assurance Maturity Model (SAMM)
The OWASP Software Assurance Maturity Model (SAMM) [https://owaspsamm.org] is a framework that can be used to help an organization understand how it is doing for secure development and provide prescriptive guidance on what might be the next steps in your program.
SAMM covers Governance, Construction, Verification, and Operations. It is a larger scale than just the Software Development Lifecycle (SDLC), and helps provide invaluable insight into the maturity of your software development.
We can conduct a SAMM review for your organization that would consist of document and process review and discussions with the people that have responsibilities related to software development and support in your organization.
At the conclusion of the review, we'll provide you with a presentation of the process, observations, scoring, and recommended three-phase roadmap.
Architecture Review & Threat Modeling
Whether you are interested in an architecture review or threat modeling exercise, we can help review the design decisions, assumptions, security controls, and business flows within your application or system.
The process includes reviewing any existing documentation and several discussions with people filling the roles of business analyst, architect, developer, and others.
The result of the review will be a logical architecture diagram with your system components, connections, weaknesses, and controls. This diagram will be included in a report that contains the process, a controls analysis, and recommendations.

Trusted Advisor
The trusted advisor service provides you with someone who can help you build and expand on your software security program and activities. The advisor is available for an agreed upon average number of hours a week/month to help with making informed decisions, building presentations, reviewing documentation, and other important tasks.
All work is done remotely by email, phone, video conference, slack, teams, we can use the medium your team uses to communicate. You can leverage someone with experience building programs at a fraction of the cost of attempting to hire them full time.
The advisor can help play a key role in providing years of experience in different roles like developer, architect, tester, management, and consultant in different industries. We can help provide that needed experience as you need it, when you need it to advance your program and improve your software security.

Process Integration & Metrics
We can help integrate security into your existing processes. To successfully incorporate security into your development processes, it needs to be integrated with how daily work is done in the existing tooling if at all possible. Sometimes those tools and processes don't exist yet, we can help build and integrate them for you.
Want your teams to learn how to perform secure design review or threat modeling within their existing process? We can help teach them how to do this.
Need help trying to figure out how to measure progress or improvements, we can help provide recommendation and guidance in data correlation and analysis.
